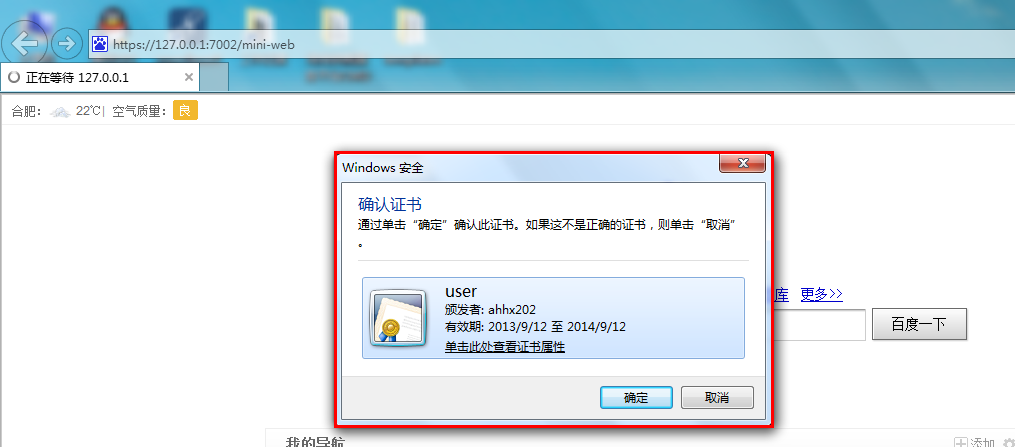
WebLogic11g-单双向SSL配置(以Springside3为例)
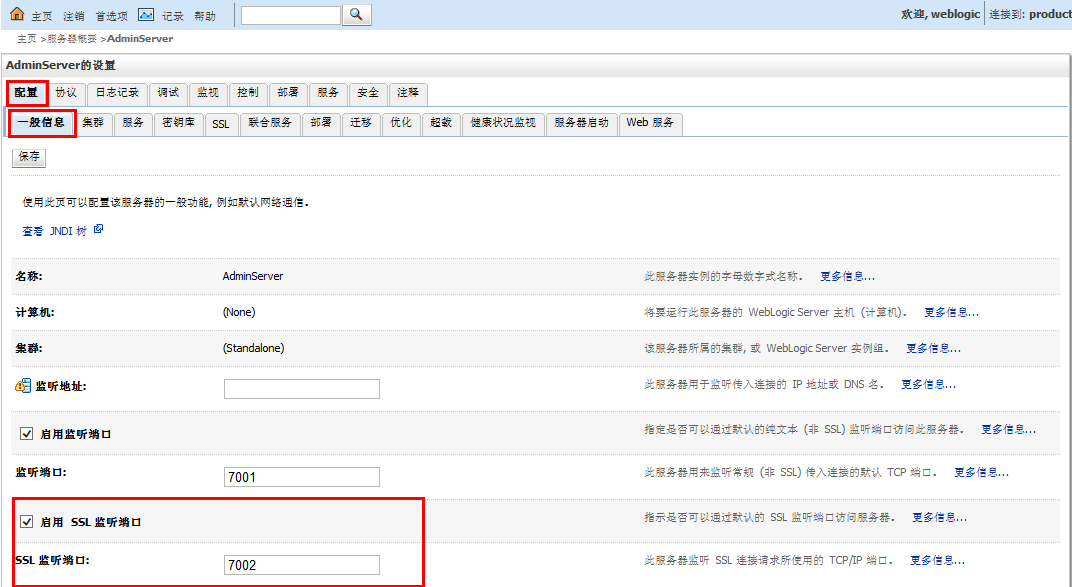
2、观察weblogic方便开发部署提供的演示秘钥库
(秘钥库位置为:\weblogic11\wlserver_10.3\server\lib)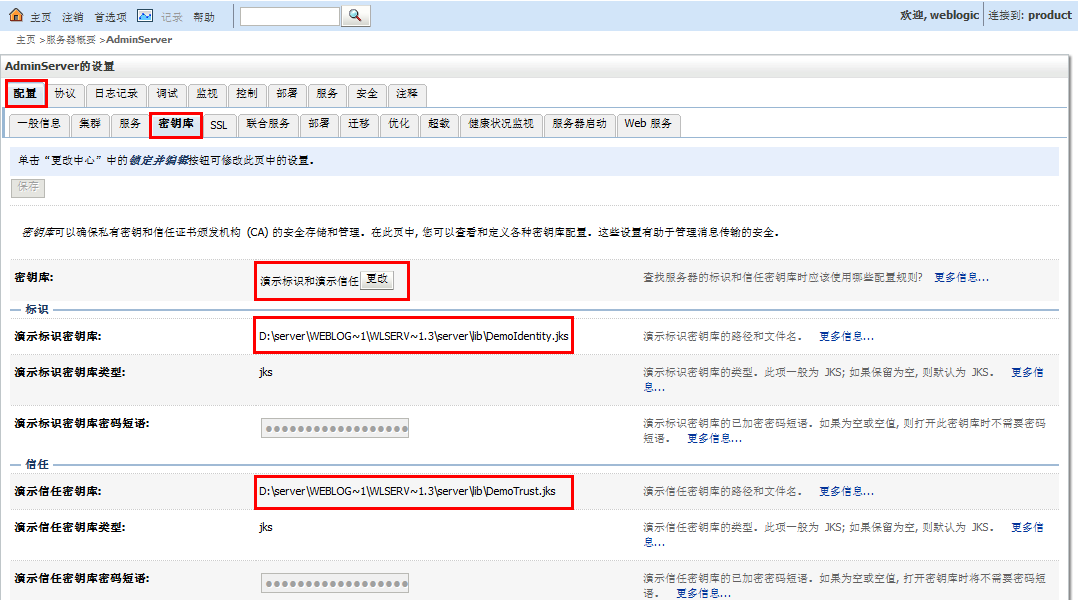
3、观察ssl的默认演示配置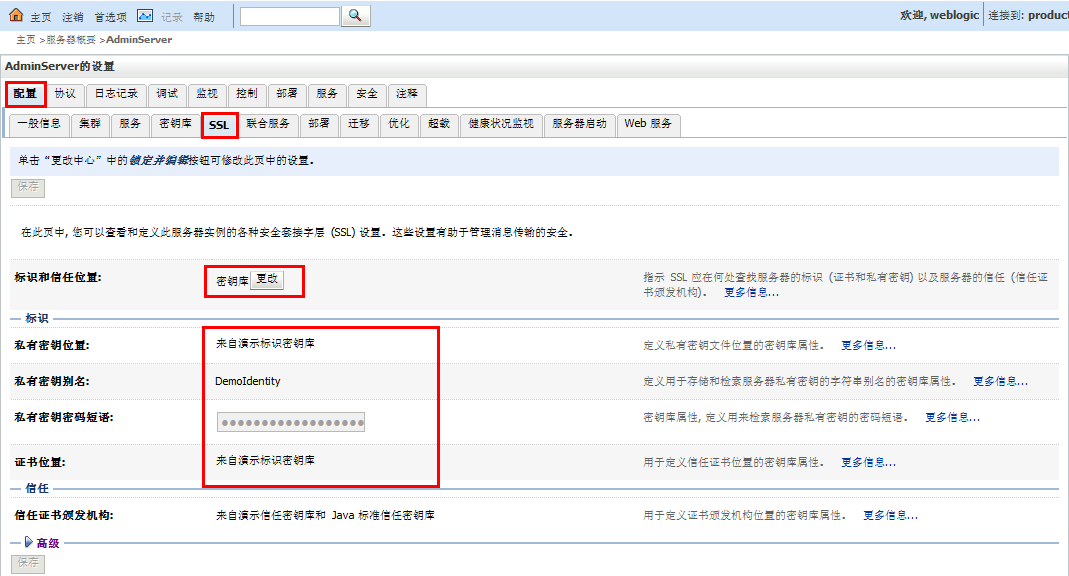
那么在开发过程中,只需要在第一幅图上勾选“启用ssl监听端口”即可。
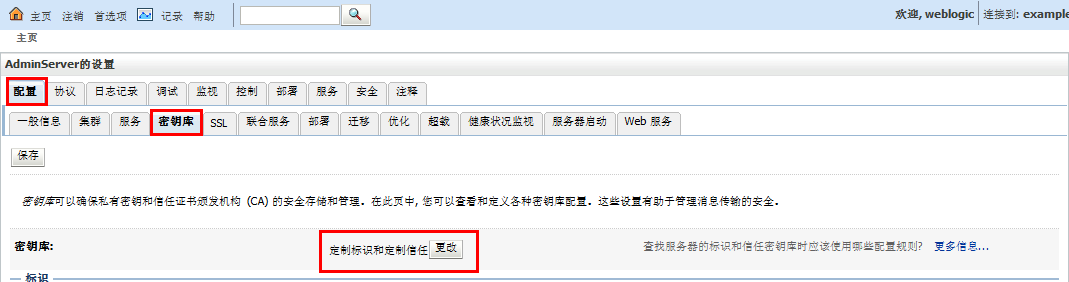
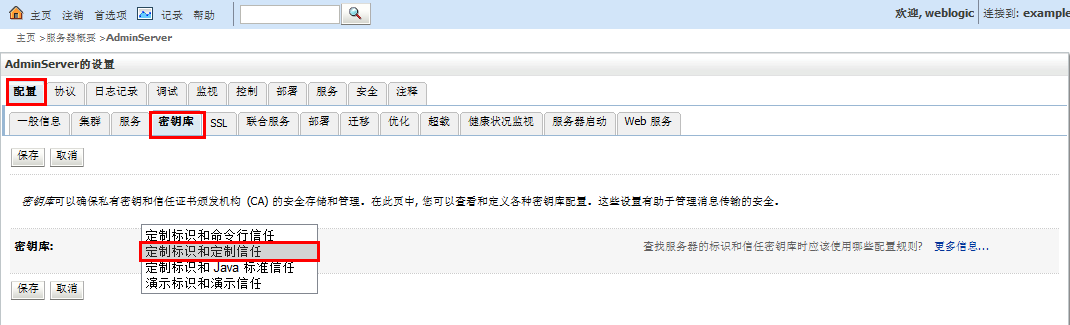
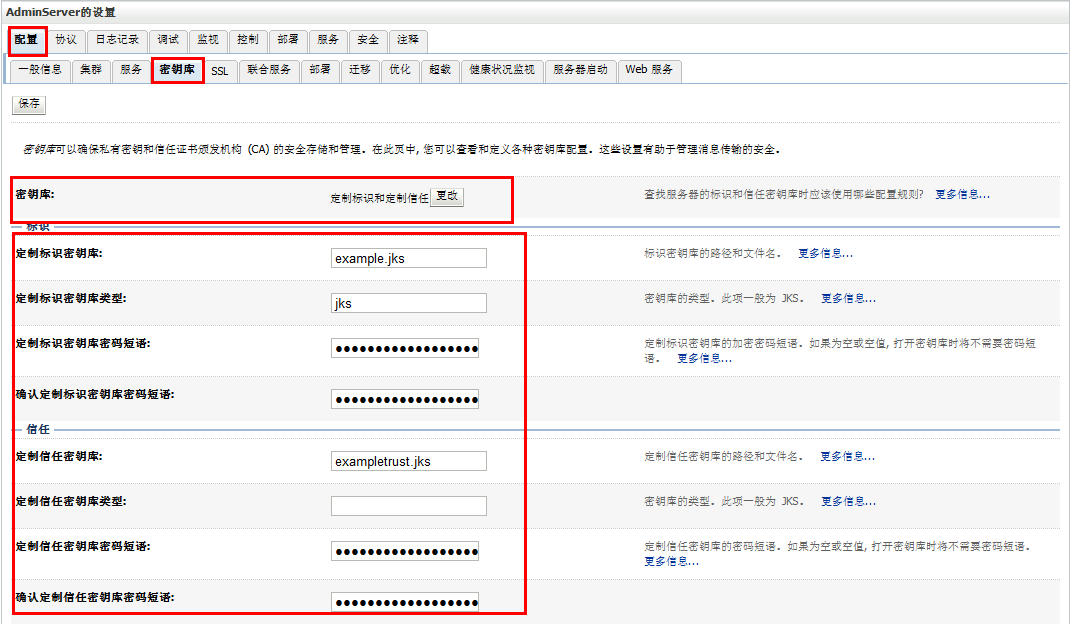
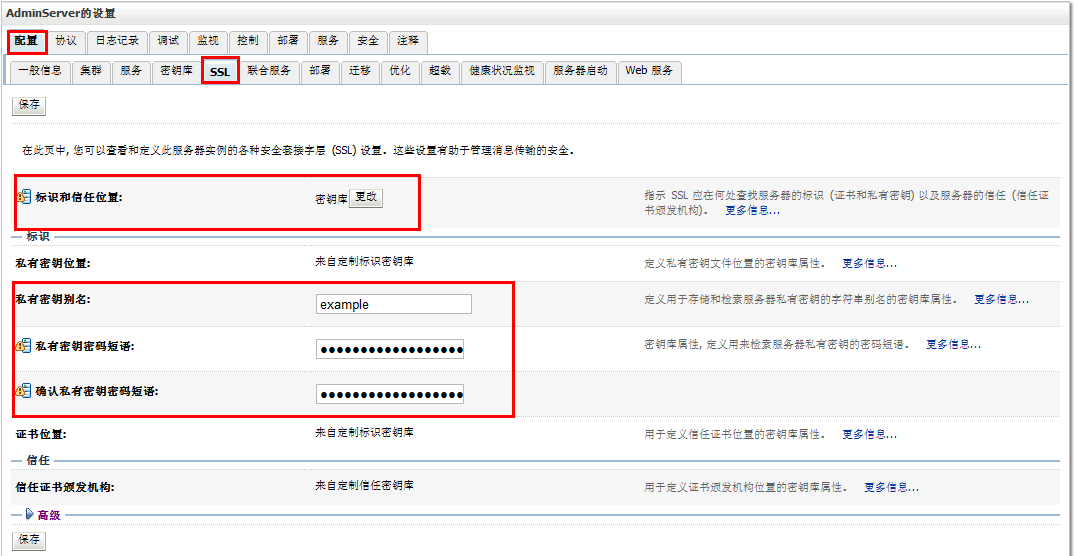
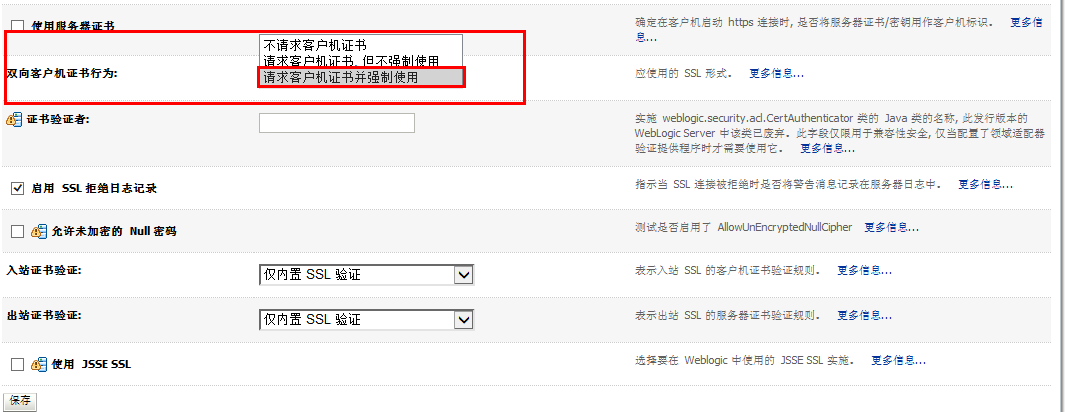
正式环境中,有哪些变化呢?主要就是更改上面2、3图中的配置,改为实际的秘钥库、以及根据实际的秘钥库来配置SSL。
网上可以搜到很多weblogic配置ssl相关资料,但是很多配置在实际环境中,都是跑不起来的。究其原因,有两点(1、需要去ca认证中心对产生的证书请求进行签证;2、更有甚者,直接使用keytool来制作,压根没提签证这回事)。weblogic配置ssl,需要标识(私钥和数字证书)、信任(可信证书颁发机构颁发的证书),所以光通过产生私钥直接配置肯定是不行的。
下面是具体的步骤:
1、下载openssl工具
这里使用openssl工具来制作这些秘钥、ca根证书等等。
openssl的windows安装文件放在网盘中,如果有需要随时下载。网盘地址为:
http://pan.baidu.com/share/link?shareid=421723979&uk=3222190371
我的安装路径为:D:\work\OpenSSL
安装之后,打开cmd进入到bin目录下,即D:\work\OpenSSL\bin。开始制作根证书、秘钥等。
2、制作CA根证书
D:\work\OpenSSL\bin>openssl genrsa -out ca/ca-key.pem 1024Loading 'screen' into random state - doneGenerating RSA private key, 1024 bit long modulus...............++++++...++++++e is 65537 (0x10001)D:\work\OpenSSL\bin>openssl req -new -out ca/ca-req.csr -key ca/ca-key.pem -config openssl.cnfYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [AU]:CNState or Province Name (full name) [Some-State]:AHLocality Name (eg, city) []:HFOrganization Name (eg, company) [Internet Widgits Pty Ltd]:CAROOTOrganizational Unit Name (eg, section) []:CACommon Name (eg, YOUR name) []:ahhx202Email Address []://这里直接回车,不配置Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []://这里直接回车,不配置An optional company name []:这里直接回车,不配置D:\work\OpenSSL\bin>openssl x509 -req -in ca/ca-req.csr -out ca/ca-cert.pem -signkey ca/ca-key.pem -days 3650Loading 'screen' into random state - doneSignature oksubject=/C=CN/ST=AH/L=HF/O=CAROOT/OU=CA/CN=ahhx202Getting Private key
D:\work\OpenSSL\bin>keytool -genkey -alias example -validity 365 -keyalg RSA -keysize 1024 -keypass 123456 -storepass 123456 -keystore example.jks您的名字与姓氏是什么? [Unknown]: ahhx202您的组织单位名称是什么? [Unknown]: CAROOT您的组织名称是什么? [Unknown]: CA您所在的城市或区域名称是什么? [Unknown]: HF您所在的省/市/自治区名称是什么? [Unknown]: AH该单位的双字母国家/地区代码是什么? [Unknown]: CNCN=ahhx202, OU=CAROOT, O=CA, L=HF, ST=AH, C=CN是否正确? [否]: yD:\work\OpenSSL\bin>keytool -certreq -alias example -sigalg MD5withRSA -file example.csr -keypass 123456 -keystore example.jks -storepass 123456D:\work\OpenSSL\bin>openssl x509 -req -in example.csr -out example.pem -CA ca/ca-cert.pem -CAkey ca/ca-key.pem -days 365 -set_serial 1Loading 'screen' into random state - doneSignature oksubject=/C=CN/ST=AH/L=HF/O=CA/OU=CAROOT/CN=ahhx202Getting CA Private KeyD:\work\OpenSSL\bin>keytool -import -v -trustcacerts -keypass 123456 -storepass 123456 -alias root -file ca/ca-cert.pem -keystore example.jks所有者: CN=ahhx202, OU=CA, O=CAROOT, L=HF, ST=AH, C=CN发布者: CN=ahhx202, OU=CA, O=CAROOT, L=HF, ST=AH, C=CN序列号: c1dedc7b5ba58f41有效期开始日期: Wed Sep 11 21:37:29 CST 2013, 截止日期: Sat Sep 09 21:37:29 CST2023证书指纹: MD5: 22:26:1A:F1:A0:D8:A9:80:05:CA:12:A2:C0:EB:30:11 SHA1: CB:C2:96:74:2A:03:9B:F8:39:F2:19:D8:5D:40:95:E7:25:27:64:73 SHA256: 61:48:18:5E:49:27:13:38:69:B7:01:C1:ED:98:59:8A:B8:85:26:A8:D3:5D:2E:EC:1E:DB:7E:59:71:AB:01:34 签名算法名称: MD5withRSA 版本: 1是否信任此证书? [否]: Y证书已添加到密钥库中[正在存储example.jks]D:\work\OpenSSL\bin>keytool -import -v -trustcacerts -storepass 123456 -alias example -file example.pem -keystore example.jks证书回复已安装在密钥库中[正在存储example.jks]D:\work\OpenSSL\bin>keytool -import -alias example-ca -trustcacerts -file ca/ca-cert.pem -keystore exampletrust.jks输入密钥库口令:123456再次输入新口令:123456所有者: CN=ahhx202, OU=CA, O=CAROOT, L=HF, ST=AH, C=CN发布者: CN=ahhx202, OU=CA, O=CAROOT, L=HF, ST=AH, C=CN序列号: c1dedc7b5ba58f41有效期开始日期: Wed Sep 11 21:37:29 CST 2013, 截止日期: Sat Sep 09 21:37:29 CST2023证书指纹: MD5: 22:26:1A:F1:A0:D8:A9:80:05:CA:12:A2:C0:EB:30:11 SHA1: CB:C2:96:74:2A:03:9B:F8:39:F2:19:D8:5D:40:95:E7:25:27:64:73 SHA256: 61:48:18:5E:49:27:13:38:69:B7:01:C1:ED:98:59:8A:B8:85:26:A8:D3:5D:2E:EC:1E:DB:7E:59:71:AB:01:34 签名算法名称: MD5withRSA 版本: 1是否信任此证书? [否]: Y证书已添加到密钥库中
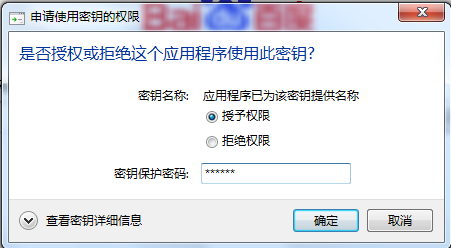
<!-- http安全配置 --><s:http auto-config="true" use-expressions="true"><s:intercept-url pattern="/css/**" filters="none" /><s:intercept-url pattern="/img/**" filters="none" /><s:intercept-url pattern="/js/**" filters="none" /><s:intercept-url pattern="/account/user!save*" access="hasAnyRole('ROLE_修改用户')" /><s:intercept-url pattern="/account/user!delete*" access="hasAnyRole('ROLE_修改用户')" /><s:intercept-url pattern="/account/user*" access="hasAnyRole('ROLE_浏览用户')" /><s:intercept-url pattern="/account/role!save*" access="hasAnyRole('ROLE_修改角色')" /><s:intercept-url pattern="/account/role!delete*" access="hasAnyRole('ROLE_修改角色')" /><s:intercept-url pattern="/account/role*" access="hasAnyRole('ROLE_浏览角色')" /><s:x509 user-service-ref="userDetailsService" subject-principal-regex="CN=(.*?)$"/><s:form-login login-page="/login.action" default-target-url="/" authentication-failure-url="/login.action?error=true" /><s:logout logout-success-url="/" /></s:http>产生user账号对应的秘钥:D:\work\OpenSSL\bin>openssl genrsa -out user-key.pem 1024Loading 'screen' into random state - doneGenerating RSA private key, 1024 bit long modulus.....................................++++++..++++++e is 65537 (0x10001)根据user的秘钥产生证书请求csr文件:D:\work\OpenSSL\bin>openssl req -new -out user-req.csr -key user-key.pemYou are about to be asked to enter information that will be incorporatedinto your certificate request.What you are about to enter is what is called a Distinguished Name or a DN.There are quite a few fields but you can leave some blankFor some fields there will be a default value,If you enter '.', the field will be left blank.-----Country Name (2 letter code) [AU]:CNState or Province Name (full name) [Some-State]:AHLocality Name (eg, city) []:HFOrganization Name (eg, company) [Internet Widgits Pty Ltd]:CAROOTOrganizational Unit Name (eg, section) []:CACommon Name (eg, YOUR name) []:user//这里是指登录账号,与用户表的账号对应Email Address []:Please enter the following 'extra' attributesto be sent with your certificate requestA challenge password []:An optional company name []:使用openssl之前制作的ca根证书对证书请求文件进行签证:D:\work\OpenSSL\bin>openssl x509 -req -in user-req.csr -out user-cert.pem -signkey user-key.pem -CA ca/ca-cert.pem -CAkey ca/ca-key.pem -CAcreateserial -days 365Loading 'screen' into random state - doneSignature oksubject=/C=CN/ST=AH/L=HF/O=CAROOT/OU=CA/CN=userGetting Private keyGetting CA Private Key将签证之后的证书文件user-cert.pem导出为p12格式文件(p12格式可以被浏览器识别并安装到证书库中)D:\work\OpenSSL\bin>openssl pkcs12 -export -clcerts -in user-cert.pem -inkey user-key.pem -out user.p12Loading 'screen' into random state - doneEnter Export Password://不输入密码,为空Verifying - Enter Export Password://不输入密码,为空将签证之后的证书文件user-cert.pem导入至信任秘钥库中(这里由于没有去ca认证中心购买个人证书,所以只有导入信任库才可进行双向ssl交互)D:\work\OpenSSL\bin>keytool -import -alias user -trustcacerts -file user-cert.pem -keystore exampletrust.jks